Hello Experts,
Whats is the difference between Network Slicing and Private 5G?
Hello Experts,
Whats is the difference between Network Slicing and Private 5G?
Network slicing should not be confused with Private 5G as they have different applications in practice. Private networks (manufacturing plants, airports and ports, utility production etc) will require Dedicated Core Networks (CN).
A Dedicated CN provides the enterprise with full network isolation, bringing greater control, reliability, deterministic quality, as it is not shared with other customers.
Instead network slicing caters very well to applications such as nationwide fleet management, providing a reliable & controlled service wherever the device is located.
The logic is that “operational isolation” is sufficient for the majority of customers because 'Vertical customers could have independent monitoring, control, configuration, or even full operation capability of the network slice”. Instead, “network level isolation, means that vertical customers do not share network function or resources with the other customers” is not considered to be a fundamental requirement and is not addressed by network slicing.
Therefore network slicing assumes that only a small number of slices will be required in a national network & that they will be shared by enterprises having similar needs.
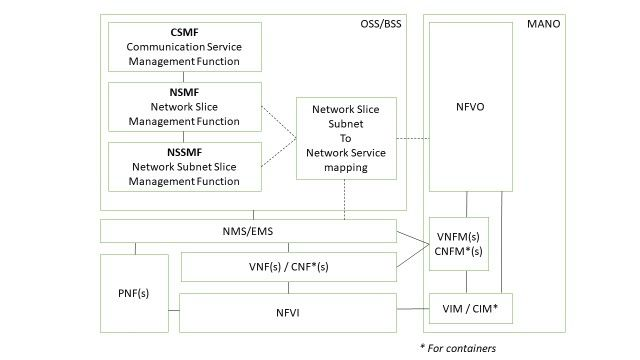
According to the information model described in 3GPP TR 28.801, a network slice contains one or more network slice subnets, each of which in turn contains one or more network functions and can also contain other network slice subnets.
· Network Slice Instance is E2E slice , that contains NFs (e.g. belonging to AN and CN).
· Network Slice Subnet can be considered as an NFV Network Service, for instantiation of a NSI that contains RAN and CN components, these components can be defined and instantiated as two NSSIs: NSSI1 (RAT1) in RAN and NSSI2 in CN.
· Network Function can be described as VNF & PNF
3GPP TR 28.801 identifies three management functions related to network slicing management, which include
· Communication Service Management Function (CSMF)
· Network Slice Management Function (NSMF),
· Network Slice Subnet Management Function (NSSMF)
CSMF manages and controls the activities of both the communication service consumer and communication service provider by converting communication requirement to network slice requirement for all deployment scenarios. The CSMF connects to the NSMF to get the NSI as a communication service and based on the NSIs provided by the NSMF, the CSMF transmit each NSI as a communication service to the exact communication service consumer.
NSMF is one of the most important network slicing management functions. The NSMF is responsible for the coordination, management, and orchestration of NSI (i.e. end-to-end NSI life cycle management). For every slice request NSMF gets slice creation approval from the network provider for instantiate the NSI and if there is no approval it discards the slice request.
NSSMF is responsible for the management and orchestration of the NSSI throughout its lifecycle. It also gets request approval from the network provider. Based on the per-slice request, the NSSMF select the required resources in forming either the AN, CN or DN NSSIs. NSSMF will get all the required resources in making the NSSI from the Network functions (NFs) then manage and control the transmission of individual NSSIs to form an NSI.
The NSMF and NSSMF will finally send request for network service to ETSI NFV MANO. But slices really span across multiple domains, such as heterogeneous access including RAN, transport, edge, and core, and in some instances data network and cloud.
Multiple NSSMF are involved to manage those underlying subnetworks. The RAN NSSMF may interface with RAN controllers to request RAN resources and the transport NSSMF may interface with an SDN orchestrator to request certain links.
Each domain may have a mix of physical and virtual functions and resources, which are described in an E2E hybrid inventory automatically updated with new instances and relationships. Alarms and events are collected and processed by service assurance with a combination of topology correlation and artificial intelligence to identify patterns.