-
A lot is happening in security industry in 2023, especially around security data - its collection, processing, and whether or not it’s siloed from the rest of the business data.
-
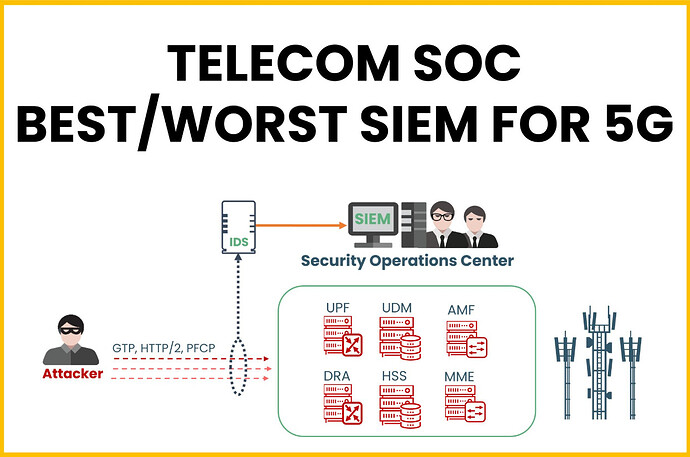
However, the reality is that you can have the best SIEM in the world, but if you lack the right raw data at the source, your ability to quickly detect and respond to security events is severely limited.
For example, based on our knowledge, roughly 10% to 15% of Telecom Security Operations Centers have sufficient security visibility over mobile network assets. Some organizations claim to have their most critical assets (like HSS, MME, etc.) onboarded onto their SIEM, but this often barely covers what is happening on the management interfaces of these platforms and includes only basic log collection from OSS/BSS systems.
-
Here’s a brief self-check for confidence:
- Would a hacker gaining initial access via MNO Roaming Partners be noticed by your SOC?
- Would the execution of registering malicious network functions be flagged?
- Could they evade defenses with home routing bypass?
- Would an attack on the Service-Based Interface to access credentials go unnoticed?
-
Or would the first red flag be raised only when the attacker commits an impact in the form of a Network Denial of Service?
-
If you’re unsure about these answers, it might be time to check if your SOC truly has visibility over telecom assets.
-
Last year, MITRE published the 5G Hierarchy of Threats, named FiGHT, it includes:
- 15 tactics, one of which is unique to telecoms—Fraud
- 86 techniques specific to 5G.
*That’s quite a lot to keep an eye on, isn’t it?
Enterprise networks have many valuable sources of security data, and telecom networks offer even more. Thanks to the network control plane, one can achieve very precise and efficient visibility over telecom assets. Regardless of which SIEM you use for 5G, it’s time to leverage signaling for threat detection and response.
LinkedIn: ![]()