Dear Members,
We have recently received a request to restrict a locally employed application due to identified malicious activities. Our network infrastructure relies on Sandvine for managing both Gi and fixed fiber traffic, with all external traffic from our subscribers passing through Sandvine elements.
During the assessment of the application’s behavior, we encountered challenges in detecting the deeplinks it utilizes. However, leveraging the Sandvine live view and an Android application named “PCAPdriod,” we successfully identified the deeplinks associated with the application for detection purposes.
A rule was promptly established; nevertheless, the application subsequently altered the URL it employs for deeplinks related to its content. As a result, we find ourselves in the position of continually blocking the application URL on an hourly basis to ensure ongoing prevention.
In light of this, I am seeking a more permanent solution to block the application without the need for hourly URL detection. The current approach involves the creation of an object on Sandvine, with URL items added to it for the identified deeplinks of the application. Detection of these links is achieved through either the live view on Sandvine or the utilization of PCAPdriod.
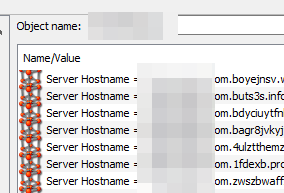
A snippet of the items incorporated under the object is provided below for your reference.
Your insights and recommendations on achieving a more efficient and sustainable resolution to this matter would be greatly appreciated.