![]() Ever connected to airport or café Wi-Fi without a password and wondered — “Is this safe?”
Ever connected to airport or café Wi-Fi without a password and wondered — “Is this safe?”
Let’s face it: Open Wi-Fi networks are everywhere — convenient, but historically insecure.
![]() But what if your data could still be encrypted, even without entering a password?
But what if your data could still be encrypted, even without entering a password?
That’s where OWE (Opportunistic Wireless Encryption) steps in — offering encryption without authentication.
Think of it like HTTPS for Wi-Fi: no login prompt, yet your data stays encrypted over the air.
![]() What is OWE?
What is OWE?
OWE is part of the WPA3 standard, replacing legacy “open” Wi-Fi with enhanced open networks.
It uses Diffie-Hellman key exchange to create a unique encrypted session per client, even on an SSID without a password.
So even though the SSID looks “open,” your communication is far from exposed.
![]() How OWE Works (High-Level + OTA View)
How OWE Works (High-Level + OTA View)
![]() Client connects to an OWE-enabled SSID (visible as “open”).
Client connects to an OWE-enabled SSID (visible as “open”).
![]() Over the air, you’ll observe:
Over the air, you’ll observe:
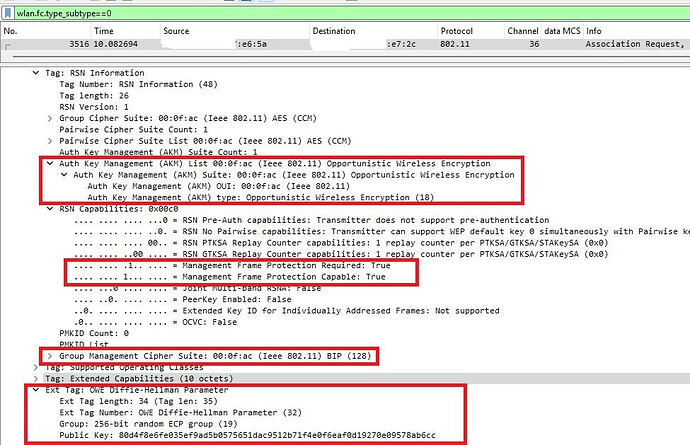
• RSN IE with AKM Suite Type = 18 (OWE)
• PMF is mandatory → mfpc=1, mfpr=1
• A separate Diffie-Hellman Key Exchange IE present in the association and AP Beacon
![]() A unique encryption key is generated per client → no more shared keys, no passive sniffing.
A unique encryption key is generated per client → no more shared keys, no passive sniffing.
![]() Why OWE Is a Game-Changer
Why OWE Is a Game-Changer
![]() Protects user traffic even without password authentication
Protects user traffic even without password authentication
![]() Blocks packet sniffing and passive eavesdropping
Blocks packet sniffing and passive eavesdropping
![]() Makes public Wi-Fi far more secure without impacting usability
Makes public Wi-Fi far more secure without impacting usability
It’s transparent to the user, but a nightmare for attackers hoping for an open field.
![]() Where OWE Fits Best
Where OWE Fits Best
• ![]() Airports & Stations – Fast onboarding with encryption
Airports & Stations – Fast onboarding with encryption
• ![]() Hotels & Cafes – No password friction, safer connections
Hotels & Cafes – No password friction, safer connections
• ![]() Universities, Libraries – Easy access without compromising security
Universities, Libraries – Easy access without compromising security
• ![]() Smart Cities – Foundation for secure public infrastructure
Smart Cities – Foundation for secure public infrastructure
![]() Bonus Tip: Sniff It Yourself
Bonus Tip: Sniff It Yourself
In Wireshark, look for:
![]() RSN IE → AKM = 00-0F-AC:18 (OWE)
RSN IE → AKM = 00-0F-AC:18 (OWE)
![]() PMF → Both Capable (mfpc=1) and Required (mfpr=1)
PMF → Both Capable (mfpc=1) and Required (mfpr=1)
![]() Diffie-Hellman Key Exchange IE → uniquely seen in OWE association flows
Diffie-Hellman Key Exchange IE → uniquely seen in OWE association flows
![]() OWE ≠ WPA2-Personal
OWE ≠ WPA2-Personal
WPA2 → Shared PSK
WPA3-Personal → Password + stronger encryption
OWE → No password, but unique session keys
![]() Final Thought
Final Thought
OWE brings zero-click encryption to public Wi-Fi—no passwords, no captive portals—just better security.
It doesn’t make open Wi-Fi completely bulletproof, but it’s a giant leap forward in protecting users without adding friction.
Think of it as invisible armor—users don’t even notice it’s there, but attackers definitely do.
Next time you’re testing or designing public SSIDs, don’t just settle for “open.”
Make it Enhanced Open with OWE.
Have you seen OWE in action or implemented it yet? Let’s connect and discuss real-world deployment experiences. ![]()
![]()
LinkedIn: ![]()