Unsourced random access (U-RA) is a new paradigm for massive access in which the packets do not include any address field for the user, which maximizes the number of useful bits that are transmitted.
Nevertheless, if U-RA approaches need to be implemented in a practical system, we need to address the problems of identification and authentication.
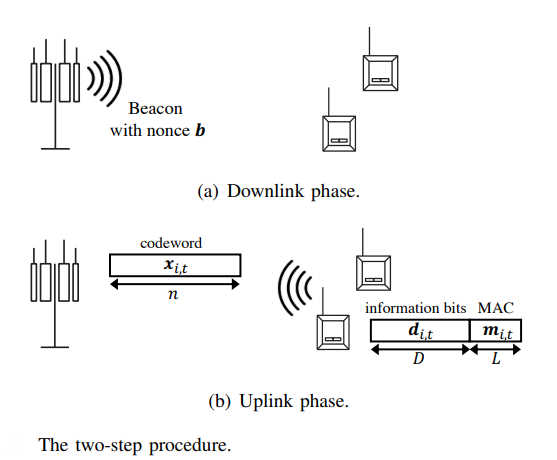
This letter presents a scheme that builds upon an underlying U-RA protocol and solves the problem of user identification and authentication. In our scheme, the users generate a message authentication code (MAC) that provides these functionalities without violating the main principle of U-RA and keeping the selection of codewords from a common codebook i.i.d. among all users.
Unlike the standard random access protocols, the proposed mechanism needs to address two types of collisions: The usual one over the wireless access channel, as well as cryptographic collisions.
The letter “How to Identify and Authenticate Users in Massive Unsourced Random Access” is published in IEEE Communications Letters, authored by Radosław Kotaba, Anders Ellersgaard Kalør, Petar Popovski, Israel Leyva-Mayorga, Beatriz Soret, Maxime Guillaud, and Luis G. Ordoñez.