In an networked environment, establishing communication between computers necessitates the assignment of unique IP addresses to each device. This can be achieved through two primary methods:
- Static IP Assignment: This involves manually configuring the IP address for a computer. Administrators manually input the specific IP address, subnet mask, gateway, and DNS server information for each device, ensuring a predetermined and fixed network configuration.
- Dynamic IP Assignment: Alternatively, devices can obtain their IP addresses automatically through a protocol designed for dynamic address allocation. The prevailing protocol for this purpose is the Dynamic Host Configuration Protocol (DHCP).
What is DHCP ?
Dynamic Host Configuration Protocol (DHCP) operates at the application layer and plays a crucial role in network configuration by distributing essential parameters such as IP addresses, subnet masks, and default gateways to hosts within a TCP/IP network. The protocol addresses the critical requirement that no two hosts on a network can share the same private IP address, underscoring the potential conflicts and issues associated with manual IP address configuration. DHCP addresses this challenge by employing temporary dynamic addresses from predefined address pools, making it inherently dynamic in nature. This dynamic allocation proves invaluable, especially in large networks, where DHCP streamlines the process of automatically assigning IP addresses and related network parameters. By doing so, DHCP significantly simplifies network administration, reducing the workload for administrators and ensuring efficient and practical IP address management.
What is a DHCP server ?
A DHCP server is the device that runs and manages the Dynamic Host Configuration Protocol information, including IP address information. In many cases, it’s the router in your home, the meaning of DHCP servers is any device that performs the Dynamic Host Configuration Protocol. DHCP servers receive the necessary information and set up the client, performing essential functions in the DHCP process.
Other important DHCP entities to understand are the DHCP client and the DHCP lease time. A DHCP client can be any device on a network; it’s the recipient of the IP address and other assigned information from the DHCP network server. A lease is simply the length of time that a Dynamic Host Configuration Protocol server allows a device to hold a particular IP address. When the DHCP lease expires, the device can receive a new IP address.
How DHCP works ?
Operating at the application layer of the TCP/IP stack, DHCP dynamically assigns IP addresses to clients and allocates TCP/IP configuration information. When a DHCP server receives a message from a client, it broadcasts a DHCP offer message over the Ethernet network, indicating the availability of the message to the client. In instances where a client cannot establish a successful connection to the DHCP server, the device may assign itself a 169.254 IP address.
The DHCP process involves several key components: the relay host, clients (users), servers, and messages. A DHCP relay agent, acting as an intermediary, forwards information packets (DHCP messages) between clients and servers when they are not on the same physical subnet.
Understanding DHCP Using Wireshark.
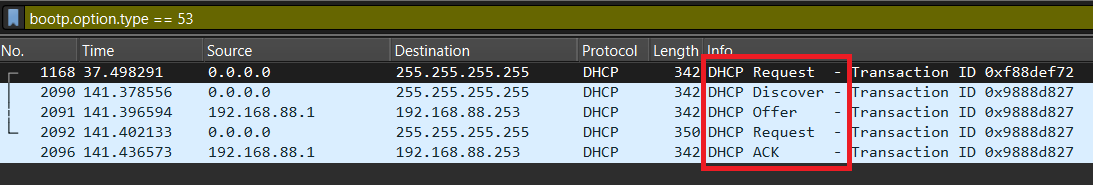
The basic process of client receiving configuration information from a DHCP server works is a four-part interaction.
As DHCP is implemented as an option of BOOTP, you can filter on BOOTP messages.
bootp.option.type == 53
In Windows, the “release” and “renew” commands are used to manage the IP address configuration of a network interface through the Command Prompt. These commands are often used to obtain a new IP address from a DHCP server or troubleshoot network connectivity issues.
ipconfig /release
This command will release the current IP address, subnet mask, and default gateway for all network interfaces.
ipconfig /renew
This command will attempt to renew the IP address configuration for all network interfaces by requesting a new IP address from the DHCP server.
There are four messages sent between the DHCP Client and DHCP Server: DHCPDISCOVER, DHCPOFFER, DHCPREQUEST and DHCPACKNOWLEDGEMENT. This process is often abbreviated as DORA (for Discover, Offer, Request, Acknowledgement).
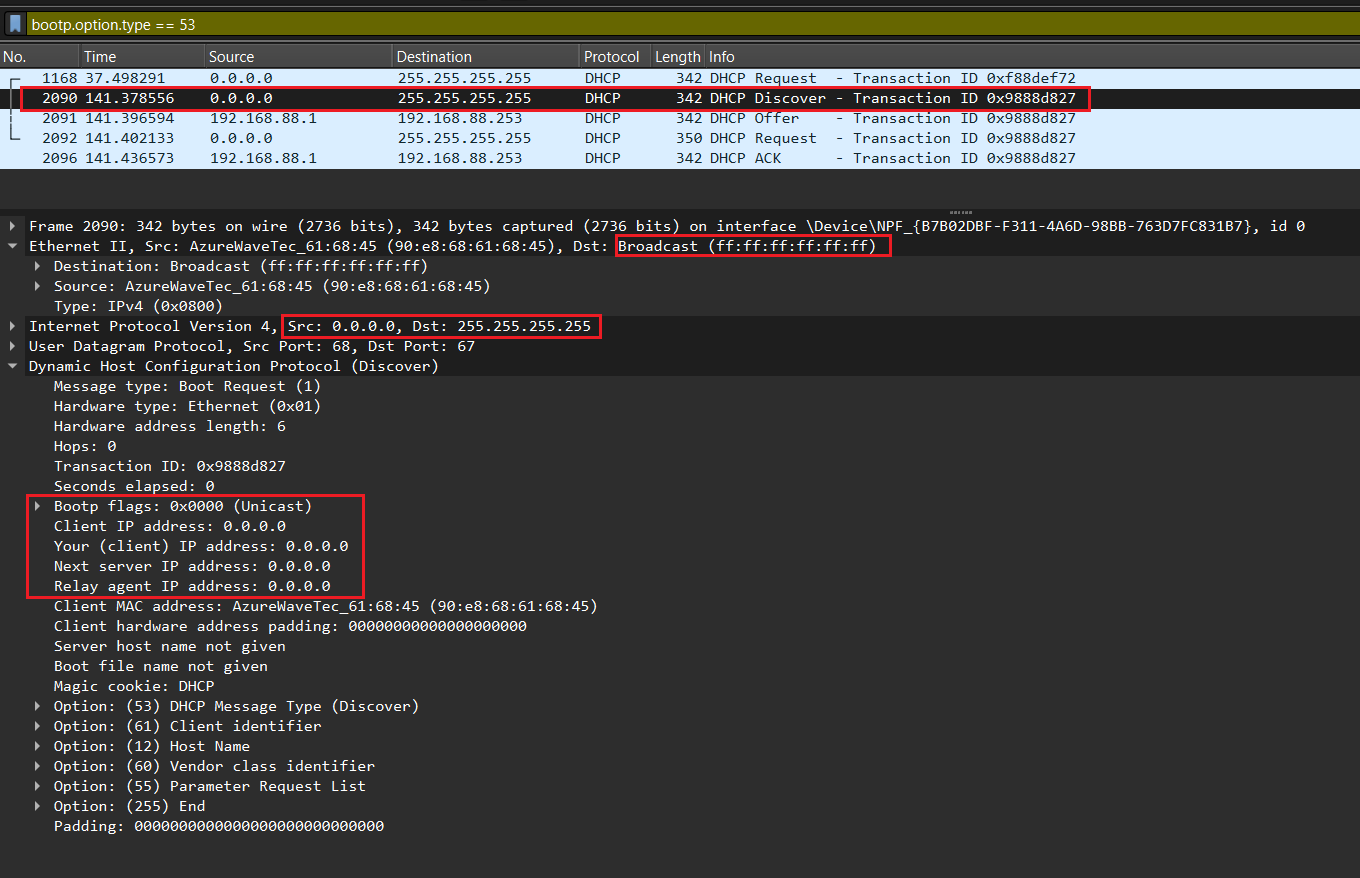
DHCP Discover.
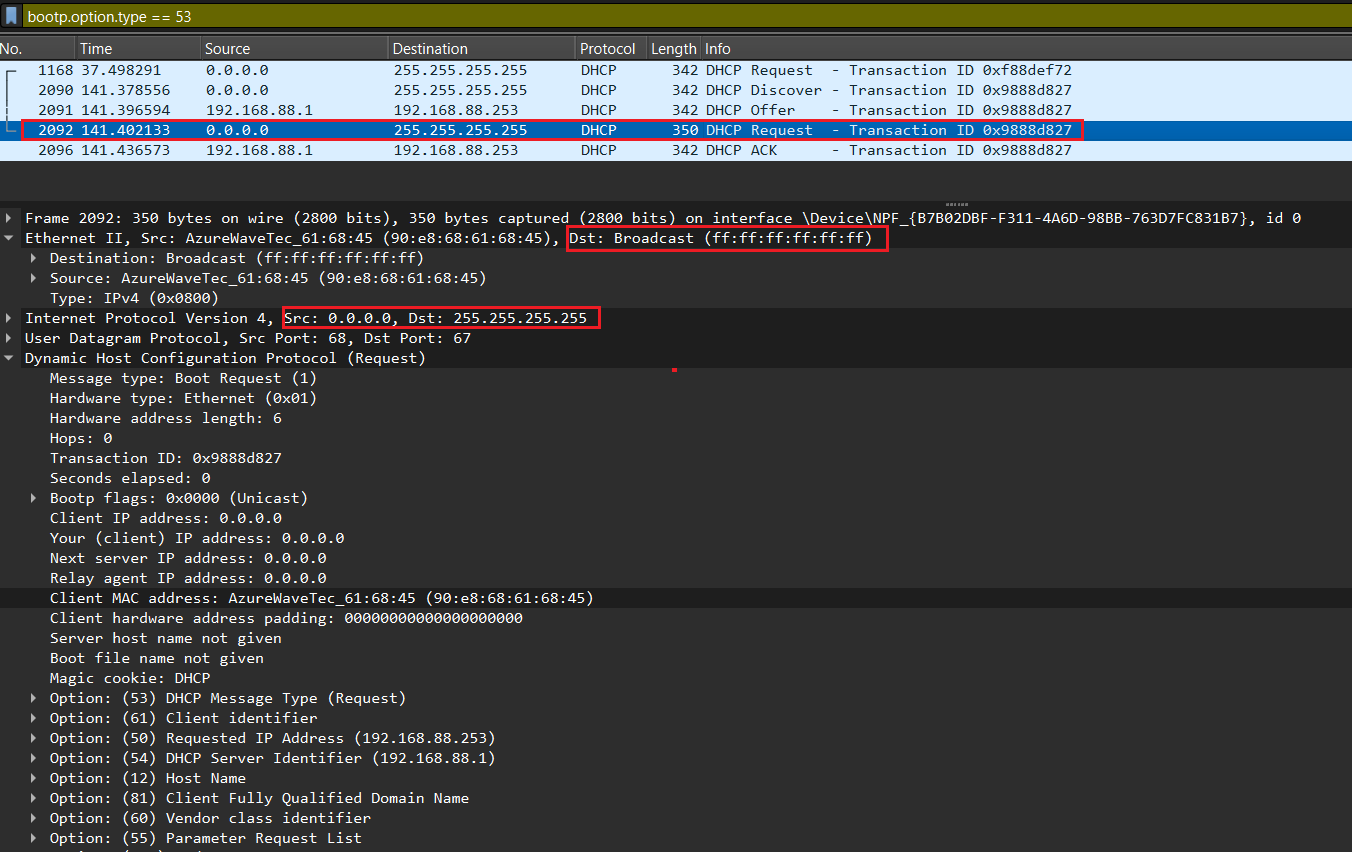
This first step is a discovery process performed by the workstation. The workstation here refers to the system that currently does not have an IP address. The purpose of this step is to discover any DHCP servers on the network that can hand out IP configuration settings. The workstation accomplishes this task by sending out a broadcast over UDP port 67 that essentially asks, “Hello, are there any DHCP servers available to help me?” This message is referred to as a DHCP Discover message.
Because the client has no way of knowing the subnet to which it belongs, the DHCPDISCOVER is an all-subnets broadcast (destination IP address of 255.255.255.255, which is a layer 3 broadcast address) and a destination MAC address of FF-FF-FF-FF-FF-FF (which is a layer 2 broadcast address). The client does not have a configured IP address, so the source IP address of 0.0.0.0 is used. The purpose of DHCPDISCOVER message is to try to find out a DHCP Server (a server that can assign IP addresses).
In a network with multiple subnets separated by routers, DHCP broadcasts typically do not traverse these router boundaries because routers, by default, do not forward broadcast traffic. However, to facilitate DHCP operations across multiple subnets, you can use a feature commonly known as “DHCP Relay” or “IP Helper.”
By using DHCP Relay or IP Helper, you can have a centralized DHCP server (or servers) serving multiple subnets, reducing the need to deploy a DHCP server on each subnet. This is particularly useful in larger networks to efficiently manage IP address assignment.
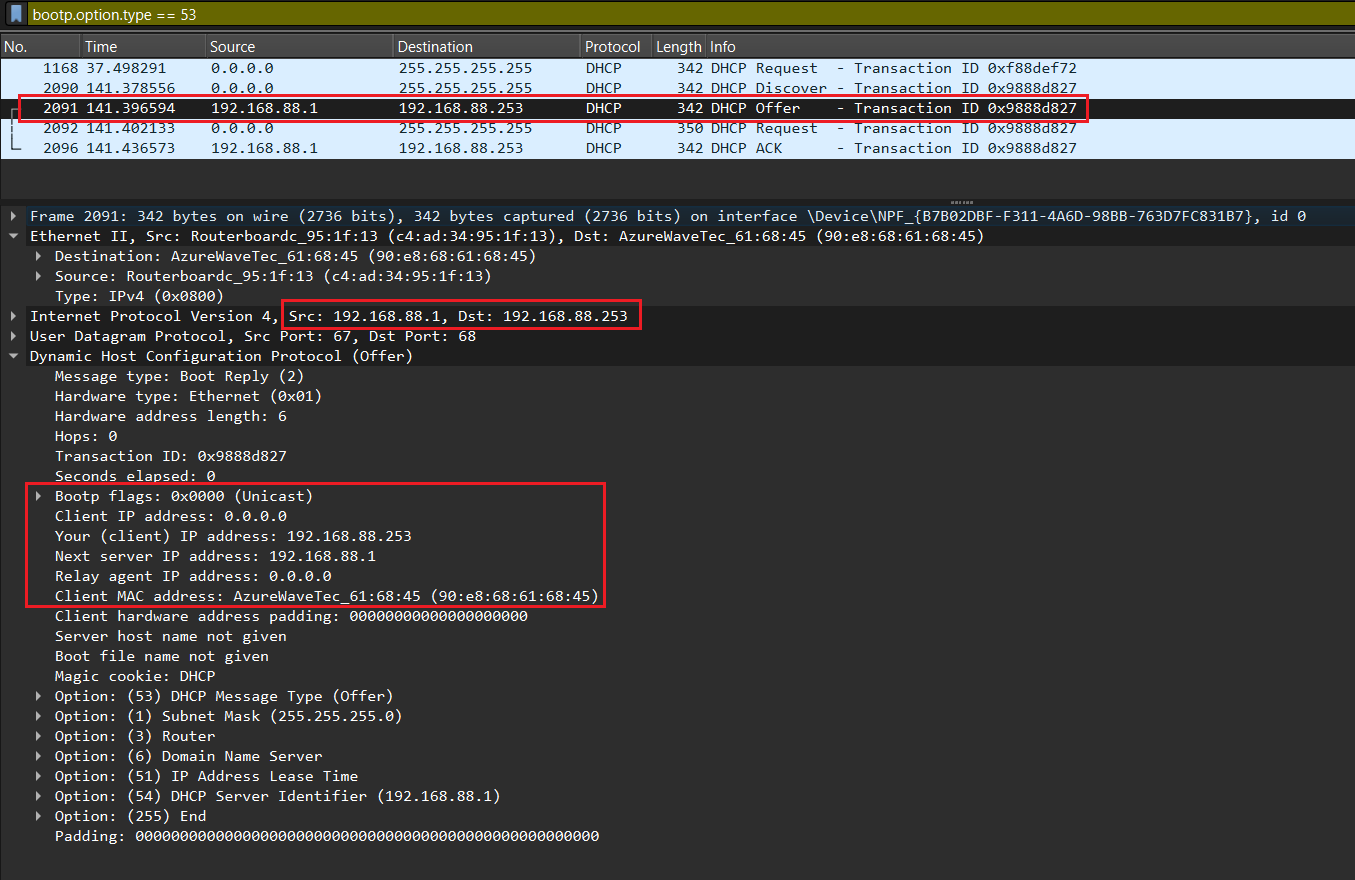
DHCP Offer.
After receiving the discover message, the DHCP Server will dynamically pick up an unassigned IP address from its IP pool and broadcast a DHCPOFFER message to the client, over UDP port 68. DHCPOFFER message could contain other information such as subnet mask, default gateway, IP address lease time, and Domain Name Server (DNS).
DHCP Request.
If the client accepts the offer, it then broadcasts a DHCPREQUEST message saying it will take this IP address. It is called request message because the client might deny the offer by requesting another IP address. Notice that DHCPREQUEST message is still a broadcast message because the DHCP client has still not received an acknowledged IP. Also a DHCP Client can receive DHCPOFFER messages from other DHCP Servers so sending broadcast DHCPREQUEST message is also a way to inform other offers have been rejected.
DHCP ACK.
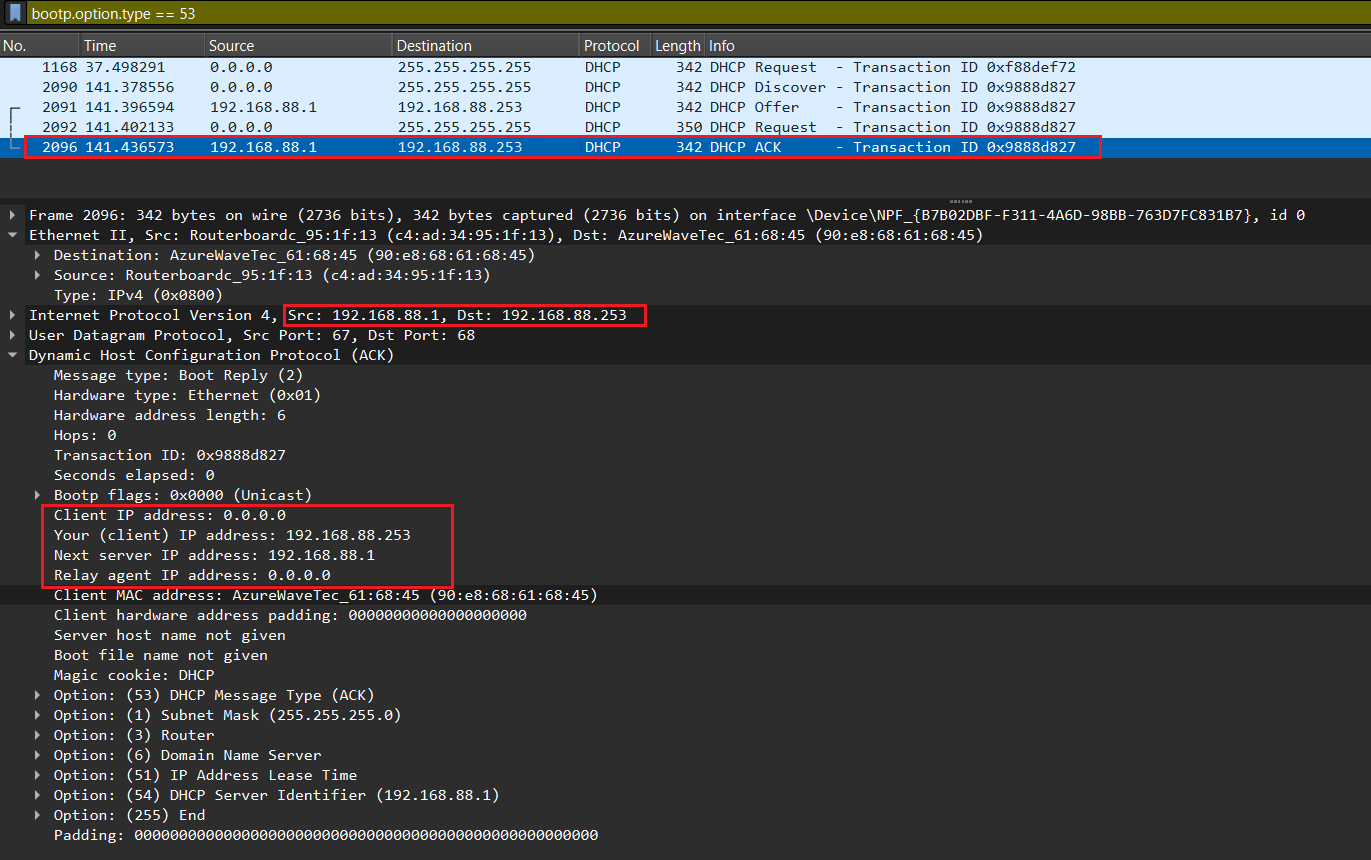
The DHCP server that was responsible for the DHCP request responds with one last broadcast to the workstation and all other DHCP servers over UDP port 68. This DHCP Acknowledgement Message tells the other DHCP servers that the new IP configuration settings are owned by this particular workstation and cannot be reused for anyone else.
After receiving DHCPACKNOWLEDGEMENT, the IP address is leased to the DHCP Client. A client will usually keep the same address by periodically contacting the DHCP server to renew the lease before the lease expires.
DHCP Renewal Process.
The DHCP request frame mirrors the typical DHCP request frame but with a crucial distinction—the client IP address field now contains the client’s existing IP. This adjustment indicates the client’s intent to renew its current IP address. Notably, this frame is transmitted as a unicast, emphasizing the client’s direct communication with the DHCP server.
DHCP Request.
The DHCP request frame is the same as the normal DHCP request frame but the client IP address field should have the client’s current IP. This is because the client is already having one IP address and it can renew the same IP address. This considered as a unicast frame.
DHCP ACK.
The subsequent frame in the renewal process is a DHCP ACK, serving as an acknowledgment of the DHCP request frame. This acknowledgment is broadcasted, confirming the successful renewal of the client’s IP address. The broadcast nature of this frame ensures that all relevant network devices are informed of the renewed IP configuration, maintaining consistency across the network.
DHCP: Security Implications and Possible Safeguards.
Because DHCP runs over UDP and because one side of all UDP communication does not have an IP address during the conversation, DHCP is an inherently insecure protocol. A hostile host can cause significant interference or compromise on a network by acting in the role of an illicit host or server (or both).
While current DHCP implementations have many vulnerabilities, there are many current proposals for improving the security of the protocol. Furthermore, there are several steps that can be taken using the current state of DHCP to operate in a more secure fashion.
Security Issues Involving Rogue DHCP Servers.
The most well-known security issues with DHCP involve the potential harm to be done by the presence of unauthorized DHCP servers on the network. Because DHCP clients depend on the information sent by the DHCP server or servers to set their most basic IP configuration information, false DHCP configuration messages can interfere with or compromise DHCP-configured hosts at the most fundamental levels. Furthermore, the host usually has no way of knowing that it is being attacked or suborned, since it depends on the DHCP server to define what the network is supposed to look like and what its place in the network is supposed to be.
Denial of Service (DoS) Attack with Rogue DHCP Server:
The simplest type of attack involving a rogue DHCP server is a denial of service (DoS) attack. The goal of this attack would be to prevent clients that depend on DHCP to obtain their configuration from joining the network. In order to do this, you would simply need to be the quickest server on the network to respond to every DHCPDISCOVER packet broadcast. You would simply respond with a DHCPOFFER that was valid but never respond with a DHCPACK to the resulting DHCPREQUEST from the client. Since the rogue server is not handing out real, valid configurations, it does not need to go through any tables to ensure that an address is not already taken; as a result, it should be easy to be the first to answer, every time. Some DHCP client implementations, however, will remember servers that initiate the lease process but don’t complete it, and will ignore further DHCPOFFERS from these servers.
Complex DoS Attack with Rogue DHCP Server:
A more complex DoS attack would give out configuration information to clients, but make it invalid in such a way that clients that accepted it would not be able to communicate correctly. Offering addresses in an entirely different subnet often works for a more subtle effect one could provide a valid IP address and subnet mask but an incorrect gateway, thus restricting hosts access to their own subnet and no farther; frequently this will prevent the user from logging on to their login server or domain controller.
DHCP Spoofing Attack:
A clever attacker may use a rogue DHCP server as a means of gaining further access to the network or to individual hosts, rather than to conduct something so crude and obvious as a denial of service attack. The most obvious way to do this would be to configure the attacker’s IP address as the default gateway for client machines, otherwise known as DHCP spoofing. By doing this, the attacker can force all of the target machine’s traffic that is outbound from the local subnet to travel through the attacker’s machine. If the attacker reads the packets and then passes them on to the correct gateway, the target is unlikely to notice the situation. However, the attacker is now able to read all of the target’s outbound traffic, even on a switched network that might foil most attempts at traffic sniffing.
DNS Poisoning Attack:
Criminals can record data transfers via the gateway in order to obtain sensitive information. This is also referred to as a man-in-the-middle attack. The downside of this exploit is that the attacker is only able to read the outbound side of any conversations, since the inbound reply traffic will still be passed directly from the real gateway to the target machine.
Another exploit would be to set an incorrect DNS server on network clients. The attacker sets his own machine’s IP address as the DNS server, and then answers DNS requests for client machines just like a real DNS server. However, for certain sites she can provide an incorrect IP address, directing the client to her own web server. With a clever false homepage for a service, this would make for a virtually undetectable type of password fishing.
Denial-of-Service Attack through Incorrect Address Assignment:
The assignment of incorrect addresses, in contrast, can lead to a denial-of-service attack, resulting in the paralysis of the entire network. DHCP snooping prevents malicious servers from establishing contact.
Accidental Rogue Servers.
It’s not even necessary that a rogue server be malicious in intent to cause substantial disruption to a network. In fact, probably the most common rogue server scenario usually occurs accidentally. In networks where customers are allowed to connect their own equipment to the network, it is a relatively common occurrence to have an inexperienced user connect the wrong port of an appliance-type device, such as a home or small office router that has DHCP server functionality, inadvertently exposing the network to broadcast DHCP responses from the device which will interfere with other clients use of the network unless steps are taken to block unauthorized DHCP servers at the switch.
Security Measures and Concerns in DHCP Environments.
DHCP snooping, however, not only protects from criminal schemes, but also from error sources that occur through the irresponsible use of additional routers. If a new router is installed into an already existing network, it can confuse the DHCP. The new router then assigns addresses that in fact should not be assigned. This can lead to connection errors. Especially within the context of business operations, it can cause problems when employees add their own devices to the network without informing the network administrator about it.
Solution: Use Switch-Based DHCP Control Mechanisms.
There is essentially no remedy for this threat in the DHCP protocol, so mechanisms to prevent rogue DHCP servers are typically designed to operate at other layers of the network protocol stack. Protocol-aware managed ethernet switches from a number of manufacturers offer effective strategies to block DHCP responses from rogue servers. Feature names may vary from manufacturer to manufacturer, but they are sometimes collectively referred to as “dhcp snooping” features, after the name used by Cisco for its implementation.
Security Issues Involving Rogue DHCP Clients.
Even without setting up a rogue DHCP server, there are a number of ways an attacker can exploit the DHCP service on a network. On the client side, the most obvious attack again is a denial of service.
Denial of Service (DoS) Attack by Rogue DHCP Client:
There are many rogue DHCP client programs available for download that will generate a massive number of DHCPDISCOVER requests, spoofing a different MAC address for each request. The rogue client answers the resulting DHCPOFFERS and quickly the network’s DHCP servers run out of available addresses to assign to new clients. Some DHCP servers use ARP requests or PINGs periodically to query the addresses they’ve given out and see which ones can be de-allocated and added back to the pool of available addresses. It would be possible for a rogue client to listen on all of the IPs it has been assigned and answer such requests, but in practice DHCP servers generally cannot recover non-answering addresses nearly as fast as a rogue client can request new ones.
Usurping the Place of an Existing Machine:
A more subtle move by a rogue client would be to attempt to usurp the place of an existing machine on the network, especially a machine such as a server that gets its IP via DHCP. The attack begins when the target machine is shut down, or the attacker may use a conventional DoS attack to render the target temporarily incapable of communicating on the network. The attacker then requests to “renew” the IP lease of the target machine, effectively usurping its IP address. By combining this move with a DHCP DoS attack, the attacker can prevent the target from re-taking its accustomed IP address.
Unauthorized Gain of Service on the Network:
A rogue DHCP client may also be used simply to gain service on a network where it does not belong. If the network has no security in place to restrict access to DHCP, this would seem to be more like taking advantage of their generosity than a true network exploit.
Modifying DHCP Packets on the Wire:
Another method of exploiting the DHCP service would be to modify the DHCP packets traveling on the wire. This is made easier because DHCP is a UDP-based service and thus has no error checking provided by the transport layer. This type of attack could be used to prevent clients from getting or renewing a lease on an address, or could be used in combination to facilitate other types of attacks.
Suggestions for Securing Networks that use DHCP.
Implement Switches and Prevent MAC Spoofing:
Implement switches in place of hubs and ensure that your switches prevent MAC address spoofing. Many of the possible DHCP attacks depend on or are facilitated by MAC spoofing techniques.
Authorize DHCP Servers in Active Directory:
Allow only authorized DHCP servers to operate in your network. Use Active Directory to manage and authorize DHCP servers, ensuring that only legitimate servers provide IP configurations to clients.
Utilize Active Detection for Rogue DNS Servers:
Implement active detection techniques to identify and mitigate potential rogue DNS servers. Regularly scan the network for unauthorized DNS servers that may pose security risks.
Block DHCP Ports at the Firewall:
Enhance security by blocking DHCP traffic (UDP ports 67 and 68) at the firewall separating your internal network from the Internet. This prevents unauthorized DHCP servers from responding to client requests.
Use MAC Address Lists for DHCP Leases:
Maintain a list of authorized MAC addresses on the DHCP server. Only devices with MAC addresses listed on the server are allowed to obtain DHCP leases, reducing the risk of unauthorized devices on the network.
Avoid Using DHCP for DNS Configuration:
While DHCP is commonly used to distribute DNS server addresses, consider avoiding this practice. The National Security Agency recommends against it due to potential abuse. Manually configure DNS addresses on clients for better control.
Uninstall Unnecessary DHCP/BOOTP Relay Agents:
Remove DHCP/BOOTP relay agents from firewalls and routers where they are not required. This reduces the potential attack surface and prevents unintended relay agents from interfering with DHCP communications.
Assign Fixed IP Addresses with Manual Configuration:
Assign fixed IP addresses to DMZ servers, critical internal servers, and important Internet-facing clients. Manually configure the IP addresses on these machines, disabling the DHCP client service to prevent dynamic address assignment.
Disable Service Binding on Unused Interfaces:
If your DHCP server is multi-homed, disable service binding on interfaces that will not be used for DHCP client requests. This ensures that the server only responds to DHCP requests on designated and secure interfaces.
Use a Non-Domain Controller Member Server for DHCP:
Deploy DHCP services on a member server that is not a domain controller. This helps limit potential security risks associated with DHCP processes running on critical domain controllers.
Enable audit logging:
Audit logging is a feature that records the activities and events that occur on your DHCP server, such as the IP address assignments, lease renewals, configuration changes, or errors. By enabling audit logging, you can monitor your DHCP server’s performance and security, and detect any anomalies or suspicious behaviour. You can also use audit logging to troubleshoot any issues or problems that may arise on your DHCP server, and generate reports or alerts based on the log data.
Consider Authentication Protocols (e.g., PPPoE):
Implement access protocols such as PPPoE that require authentication to a RADIUS server before assigning an IP address. This adds an extra layer of security, especially in environments with limited physical security or high client mobility.
For comprehensive guidance on implementing and configuring DHCPv4 and DHCPv6 in a small to medium-sized business network, along with insights into their operations and troubleshooting tips, please visit the following link:
http://vapenik.s.cnl.sk/pcsiete/CCNA2/08_DHCP.pdf
This resource covers topics ranging from setting up DHCPv4 and DHCPv6 across multiple LANs, configuring routers as DHCP servers and clients, to troubleshooting.
LinkedIn: ![]()