The Open Systems Interconnection (OSI) model is a conceptual framework that divides network communications functions into seven layers each responsible for specific functions. Sending data over a network is complex because various hardware and software technologies must work cohesively.
The OSI data model provides a universal language for computer networking, so diverse technologies can communicate using standard protocols or rules of communication. Every technology in a specific layer must provide certain capabilities and perform specific functions to be useful in networking. Technologies in the higher layers benefit from abstraction as they can use lower-level technologies without having to worry about underlying implementation details.
The layers 5, 6 and 7 of the model are given next.
Layer 5: The Session Layer.
When two computers or networked devices need to communicate, the Session Layer (also called the network dialogue controller) comes into play, managing the setup, coordination (including determining how long a system should wait for a response), and termination between the applications at each end of the session. Services provided by the Session Layer include authentication and reconnections after an interruption, contributing to the uninterrupted flow of data transmission.
Essentially, the session layer controls the connection between computers, monitoring dialogues, and establishing, controlling, and ending sessions between local and remote applications. It also maintains connections to prevent interruption of data transmission.
How does the session layer work ?
The Session Layer acts as an intermediary between the Presentation Layer and the Transport Layer, relaying information between these adjacent layers. To establish and maintain a connection between entities, the Session Layer performs the following tasks:
- Map the session address to the shipping address: Imagine you’re sending a package. The “session address” is like the sender’s address, and the “shipping address” is where the package needs to go. Mapping the session address to the shipping address is like making sure the sender’s details (at the session layer) match up with the lower-level details needed for the package to travel smoothly (at the transport layer). It’s about managing these details so that the information flows correctly from one layer to another, just like ensuring the right sender info is on your package for it to reach the correct destination.
- Select Quality of Service (QoS) parameters: The Session Layer is responsible for choosing and setting Quality of Service parameters, ensuring that the agreed-upon service levels are maintained during the session.
- Handle negotiations between session parameters: The Session Layer manages negotiations between entities regarding session parameters, facilitating agreement on various aspects of the communication. Think of the Session Layer like a mediator in a conversation. When two people (or entities) want to talk or share information, the Session Layer helps them agree on how they’ll communicate. It’s like making sure everyone is on the same page by handling discussions about how the conversation should go—whether it’s deciding on the language to use or how fast information should be exchanged. In short, the Session Layer makes sure everyone agrees on the rules for smooth communication.
- Transmit limited transparent user data: The Session Layer is involved in transmitting limited transparent user data, ensuring that data is transferred efficiently and transparently between entities.
- Monitor the data transfer phase: Throughout the data transfer phase, the Session Layer monitors the process to ensure the ongoing stability of the connection.
Session layer protocols.
OSI session layer protocols provide security, accuracy and safety in communication between two applications.
These protocols include:
- AppleTalk Data Stream Protocol (ADSP): ADSP is a development by Apple Inc. with multiple features that allow a network to configure itself. Additionally, two other protocols (AARP and NBP) allow connection without other setup.
- AppleTalk Session Protocol (ASP): ASP lets multiple applications be a part of one session at the same time. It assigns a session reference number to track communication.
- Password Authentication Protocol (PAP): PAP ensures security by limiting access to users. It asks for a password request. Then, it gives access upon verifying the password. It’s done at the link establishment stage.
- Point-to-Point Tunneling Protocol (PPTP): PPTP protocol is similar to a VPN, as it gives security through remote access.
- Remote Procedure Call Protocol (RPCP): This protocol serves the request-response function of the session layer, creating a client-server interface. The programmer can perform a procedure without coding the details.
- Real-time Transport Control Protocol (RTCP): This is the protocol responsible for making sure the quality of service stays high. It gives statistical information (packet counts, octet and packet loss) to users as feedback for the quality of media transmitted through a network.
- Sockets Direct Protocol (SDP): An advanced version of TCP, this shares limited data and also supports socket streams over RDMA (Remote Direct Memory Access).
- Short Message Peer-to-Peer (SMPP): SMPP works for telecommunications. It gives a flexible data transmission interface for short message communication.
- Secure Copy Protocol (SCP): SCP enables the transfer of computer files from a local host to a remote host between two remote applications.
- Socket Secure (SOCKS): SOCKS is an Internet protocol that requires authentication to authorize access. Communication happens through a proxy server.
- Zone Information Protocol (ZIP): ZIP gives access to processes and applications that relate to a certain zone. Therefore, no application with a different zone name can go to another zone.
- Call control for multimedia communication (H.245): H.245 acts as a control channel for conveying information for multimedia communication. It facilitates encryption, preference requests, jitter management and flow control within a communication session.
- Internet Storage Name Service (ISNS): ISNS automates the management and discovery of devices on a storage network. It reveals the devices on the network. It also reveals their zone names, IP addresses, and portal groups.
- Layer 2 Forwarding Protocol (L2F): Layer 2 Forwarding is a development of the Cisco systems that provides VPN connections for tunneling protocols.
- Network Basic Input Output System (NetBIOS): NetBIOS is a network protocol that gives a platform for applications on different devices to share information across a local area network.
Tearing down a session:
In the context of networking, tearing down a session refers to the process of disconnecting a communication link between two devices. This disconnection can occur through mutual agreement between the devices involved in the session. Alternatively, a session might be terminated if one party intentionally disconnects or due to an error condition. If one party initiates the disconnection, the other party is capable of detecting the loss of communication and subsequently tearing down its side of the session. This mechanism ensures that sessions are managed efficiently, allowing for controlled and orderly termination based on the intentions or conditions of the communicating parties.
Layer 6: The Presentation layer
The presentation layer plays a pivotal role in the translation and formatting of data exchanged between the network and applications.
Often referred to as the syntax layer because it maintains the proper syntax of transferred data. Acting as a translator, this layer formats and translates data for the application layer, aligning it with the syntax or semantics accepted by the application.
This layer can also handle the encryption and decryption required by the application layer, providing a crucial security layer for data in transit.
In essence, it functions as a reliable converter, transforming incoming data into an accurate, standardized format that aligns with the expectations of the application layer.
Functions of the presentation Layer.
The presentation layer is thus responsible for three general functions: translation, compression, and encryption and decryption.
Translation.
Layer 6 translates data based on the host’s needs. Different hosts represent data in diverse manners, especially when dealing with heterogeneous networks.
The data received from the application layer usually includes numbers and characters. The presentation layer then deals with translating the data into a transportable and storable data format that the receiving application can understand.
On the sender’s end, the presentation layer prepares the data in a format suitable for the application layer and potential encoding for transmission, ensuring proper structure and format for the recipient.
Compression.
Data compression reduces data size by encoding the actual number of bits that require transmission on the network. Therefore, through this, it helps speed up file transfer, save storage capacity, reduce bandwidth, and decrease costs for storage hardware.
The goal of compression in the presentation layer is to reduce the number of bits needed to represent data; the aforementioned encoding can thus be achieved by inserting a single repeat character or by removing all unneeded characters.
The process helps accelerate the rate at which data transmits to other layers. If you’re sending many files, the layer ensures that the files reach its destination quickly and without quality loss.
Encryption and decryption.
Both encryption and decryption occur at the sixth layer. Encryption converts data from a readable format, plaintext, into an unreadable format, ciphertext. However, only the user with the correct encryption key can access the data. The correct key then decrypts the data for proper display on the next layer.
The encryption occurs at the transmitter and the decryption occurs at the receiver. Both tasks are crucial to data security. Encryption and decryption provide data protection, protect against file tampering, and increase trust.
Presentation layer protocols
To perform the necessary functions, the presentation layer utilizes certain protocols, including:
- AFP (Apple Filing Protocol): AFP, a communication protocol designed for Mac-based platforms, specifically offers services to MacOS. The protocol allows computer users to share files easily over a network.
- SSL (Secure Socket Layer): SSL is an Internet security protocol that safeguards sensitive data transferred between web browsers and servers. Its sole purpose is to encrypt Internet connections and link between web clients and servers. It ensures that data passing through the OSI model remains private.
- NCP (NetWare Core Protocol): NCP is a network protocol designed for accessing files, messaging, printing, creating directories, synchronizing clocks, and executing remote commands, as well as other network service functions.
- XDR (External Data Representation): XDR is the standard for encoding and decoding data. It allows data to transfer between systems.
- NDR (Network Data Representation) : NDR provides several types of data representation and various constructed data types. Therefore, it plays a vital role in the implementation of the presentation layer.
Layer 7: The Application Layer.
The Application Layer in the OSI model is the layer that is the “closest to the end user”. This layer serves as the interface between the software application and the network. Oddly enough, applications themselves do not reside at the application layer. Instead the layer facilitates communication through lower layers in order to establish connections with applications at the other end. Web browsers (Google Chrome, Firefox, Safari, etc.) TelNet, and FTP, are examples of communications that rely on Layer 7.
The application layer includes protocols designed for end-users. For example, HTTP is a Layer 7 protocol designed to transmit data between a web server and a client.
The application layer identifies communication partners, resource availability, and synchronizes communication.
The Application Layer ensures that end-user applications can effectively communicate over the network.
Functions of the application layer.
Application Services:
This encompasses various functions within the application layer, including:
- Email Services: Function: The Application Layer is responsible for email forwarding, storage, and retrieval. It allows users to send, receive, and manage emails. Example Protocols: SMTP (Simple Mail Transfer Protocol) for sending emails, POP3 (Post Office Protocol) or IMAP (Internet Message Access Protocol) for email retrieval.
- File Transfer Services: Function: This service, operating at the Application Layer, facilitates the seamless transfer of files between Internet-connected devices on the same network. It empowers users to move files from one device to another and efficiently access files stored on remote computers or in cloud-based storage.Example Protocols: Layer 7 protocols, such as FTP (File Transfer Protocol), SFTP (Secure File Transfer Protocol), or HTTP (Hypertext Transfer Protocol), are commonly employed to implement file access and transfer services.
- Remote Hosting Services: Function: Enables the delivery of applications, files, and databases to users from remote servers. Users can log on to remote hosts and join sessions.Example Protocols: Remote Desktop Protocol (RDP) for remote access, HTTP or HTTPS for accessing web-based applications.
- Directory Services: Function: Allows users to access global information about various network services and locate data from websites through directories.Example Protocols: LDAP (Lightweight Directory Access Protocol) for accessing and maintaining directory information.
- Network Access Services: Function: Facilitates access to network resources and services. Users can interact with global network services.Example Protocols: DHCP (Dynamic Host Configuration Protocol) for IP address assignment, DNS (Domain Name System) for translating domain names to IP addresses.
- Service Advertisement: Function: Some applications’ services periodically send out advertisements, making the availability of their service known to other devices on the network. Others register themselves and their services with a centralized directory for query by other network devices seeking such services.Example Protocols: Examples of protocols involved in service advertisement include mDNS (Multicast DNS), which allows devices to announce their presence on the network, and DNS-SD (DNS Service Discovery), a protocol that complements DNS by discovering services on a local area network.
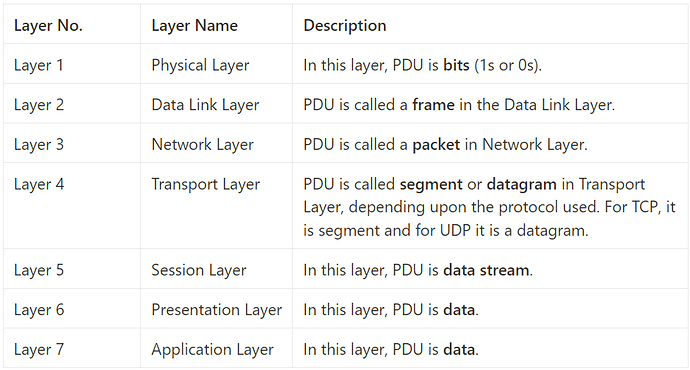
Before end this article, let’s talk about the Protocol Data Unit (PDU).
Protocol Data Unit (PDU).
The information transferred at each layer of the OSI model is encapsulated within a PDU. The PDU not only contains the actual data but also includes protocol-specific control information relevant to that layer. As the PDU moves down the layers (or up, depending on the direction of communication), each layer adds or removes its specific protocol information. The PDU is assigned a different name at each layer to signify its role in the communication process. This concept is integral to the OSI model, where the PDU adapts to layer-specific protocols and conventions. Essentially, in a computer network, the PDU represents a block of information exchanged between network end systems, playing a crucial role in the layered communication process. Different layers of the protocol stack handle distinct types of data as they facilitate communication across the network.
The following table illustrates the PDU of each protocol stack layer.
PDU
Till here, a brief of Layer 5, 6, 7 and the PDU.
LinkedIn: ![]()